February 8, 2023
There’s an old story about five blind men and an elephant. One’s holding the tail, another the trunk; others a tusk, ear, and leg. Then their boss asks each of them to describe the animal. The answers, of course, vary hugely: the man at the front thinks he’s holding a snake, the tusk guy a tortoise’s shell, and so on.

How could the men have discovered what was actually in front of them? By sharing data. Comparing their experiences (hard shell-like thing, floppy snake-like thing) and discovering that each data point is part of a larger, connected whole. If they’d talked, they might have guessed they were annoying the King of the Forest. (Prompting them, perhaps, to step out of its way.)
This, in a nutshell, is how diverse threat detection—the methods used by Getronics’ Security Operations Centre—works. Comparing and contrasting data from multiple sources and seeking to build an accurate, contextual picture that supports effective decision making within the NIST Framework of Identify—Protect—Detect—Respond—Discover.
The key watchword: diverse. Cybersecurity threats ranging from info-stealers to ransomware are incredibly diverse in form and function, and security teams defending against those threats must adapt or risk failure. Relying on a single perspective inevitably leads to missed detections or bad conclusions based on partial data, and only with multiple perspectives can the whole picture be understood.
In this briefing, you’ll see how the Getronics SOC achieves this with the combination of the SOC Visibility Triad, the MITRE ATT&CK Framework and Threat Intelligence. Let’s take hold of the elephant.
A model for visibility
Visibility is key to defenders and for a comprehensive approach the SOC Visibility Triad is used in Getronics because it puts the “elephant problem” front and centre. This model was introduced by Gartner as an effective way of thinking and communicating about how to obtain visibility and effectively detect threats.
The model contains three key components:
- Endpoint Detection & Response, collecting telemetry locally on endpoint devices
- Network Detection & Response, mirroring and analysing network traffic
- SIEM/UEBA, collecting infrastructure and application logs
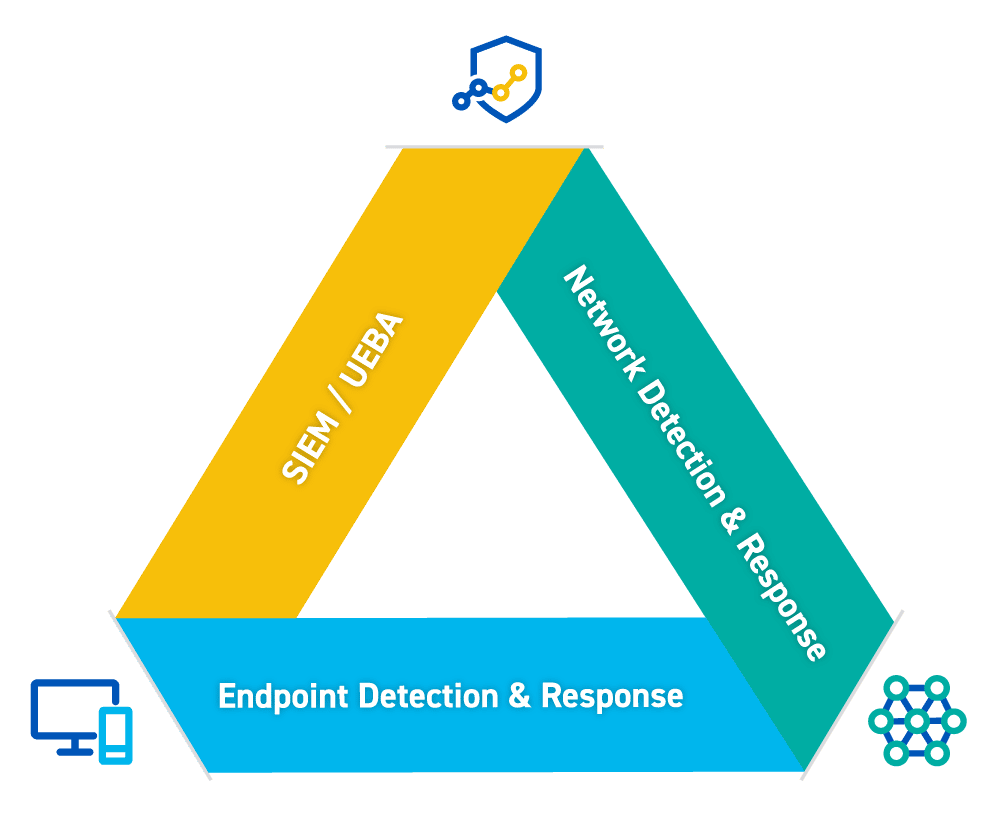
A core aspect of this model is to understand that each part of the triad can achieve 60-80% visibility, but none of them alone can meet all detection needs. An Endpoint Detection & Response solution is fantastic at stopping malware execution on a device but will not provide visibility of lateral movement on the network. Other solutions can’t cost-effectively match the correlation capability and long-term retention of a SIEM.
It’s only when combined that these three technologies provide the necessary multiple perspectives to truly enable defenders to do their best. The combined approach not only drives more detections, but it provides context and insights that make it faster to cross-check, analyse, and qualify to determine which activities are real threats and which are authorised business activities.
Understanding how threat actors operate
With the three components of the visibility triad deployed, security teams have the tools to see what is happening. However, the amount of data can be overwhelming, with billions of logs, petabytes of network information and hundreds of continuous telemetry streams from endpoint agents.
Making sense of this requires an understanding of how threat actors operate. What are their tactics, techniques, and procedures?
- How do they gain initial access to a target environment and what methods do they use for persistence so they can maintain the presence?
- How are defences evaded and how do they move across the network to a target system to find the data they want to steal and encrypt for ransom?
There has been an enormous amount of research in this field, and it has been brought together masterfully in the MITRE ATT&CK framework. This is now a central way of how security professionals learn about and communicate about the threats that they defend against.
At Getronics, the ATT&CK framework was adopted in 2018 and is an integral part of our detection engineering practise, with every detection rule in our playbook mapped against specific techniques as part of the lifecycle management from idea generation, through to development and testing, use in production and eventual decommissioning when no longer needed.
The framework also makes detection capability across different platforms measurable in a consistent way, enabling good understanding of where visibility gaps exist and where overlapping coverage provides multiple detection and analysis opportunities. For security analysts and incident responders, it provides valuable insights into the why and how of what is being observed when alarms triggers and threat hunts find unusual activities.
Threat Intelligence as a force multiplier
With excellent visibility through the visibility triad and understanding the tactics and techniques of threat actors with MITRE ATT&CK, there is still one more challenge. Trying to protect against everything everywhere will either overwhelm security teams or be prohibitively expensive. There is a very real need to focus resources where they can make the largest impact.
Threat intelligence is the answer to that challenge. By providing insight into threat actor activities, the campaigns they execute, the infrastructure they create or co-opt, the defenders can focus on the areas where the threats are most likely to manifest.
Getronics has built a threat intelligence practise which operates at three different layers:
- Operational intelligence provides indicators of compromise to detect threats such as traffic to command & control hosts and alarm enrichment to inform and speed up analysis. This is fast changing information with hundreds of thousands of data points in security control feeds being used at scale across different toolsets.
- Tactical intelligence informs processes such as detection engineering, shaping which new detection rules are developed and implemented to detect emerging threats.
- Strategic intelligence informs awareness programs, security reports and advisory services. This flows into downstream processes such as risk and vulnerability management.
Using our in-house threat intelligence platform, closely integrated with other security tools, with an in-house team of threat analysts, and by partnering with leading organizations Getronics can guide and focus the efforts to secure both own and our clients’ environments efficiently. The intelligence-led approach to security acts as a force multiplier, allowing limited resources to achieve more, to do it faster, and with better results.
A security operations centre (SOC) can be defined both as a team, often operating in shifts around the clock, and a facility dedicated to and organised to prevent, detect, assess and respond to cybersecurity threats and incidents, and to fulfil and assess regulatory compliance.
Gartner
That’s diverse detection—understanding how threat actors operate and bringing the right tools together to detect and disrupt how they carry out attacks. In summary, this security philosophy lets you:
- Understand your technology landscape and manage its vulnerabilities
- Raise awareness of threats and adjust your defences appropriately
- Detect and respond to breaches or malicious activity in real time
- Demonstrate regulatory and standards compliance
- Treat security as a whole-landscape issue, with every weak point covered
An all-round perspective. Deep and broad data sensing capabilities. And incisive skills to connect and make sense of the data generated. Taken as a whole, diverse detection gives you practically 100% coverage of everything you’d ever want to know about … which can only be a good thing. (Unless you’re an elephant with a dangerous secret.)
To see Getronics’ diverse detection smarts up close, get in touch with us today.